Technology
Meta to Test-Run Community Chats on Messenger, Facebook
By Modupe Gbadeyanka
In the coming weeks, Meta, the parent company of WhatsApp, Facebook and Instagram, will test-run a new feature known as Community Chats, on its Messenger and Facebook.
The founder of the company, Mr Mark Zuckerberg, confirmed this development in a message, noting that the feature allows users to engage themselves in real-time.
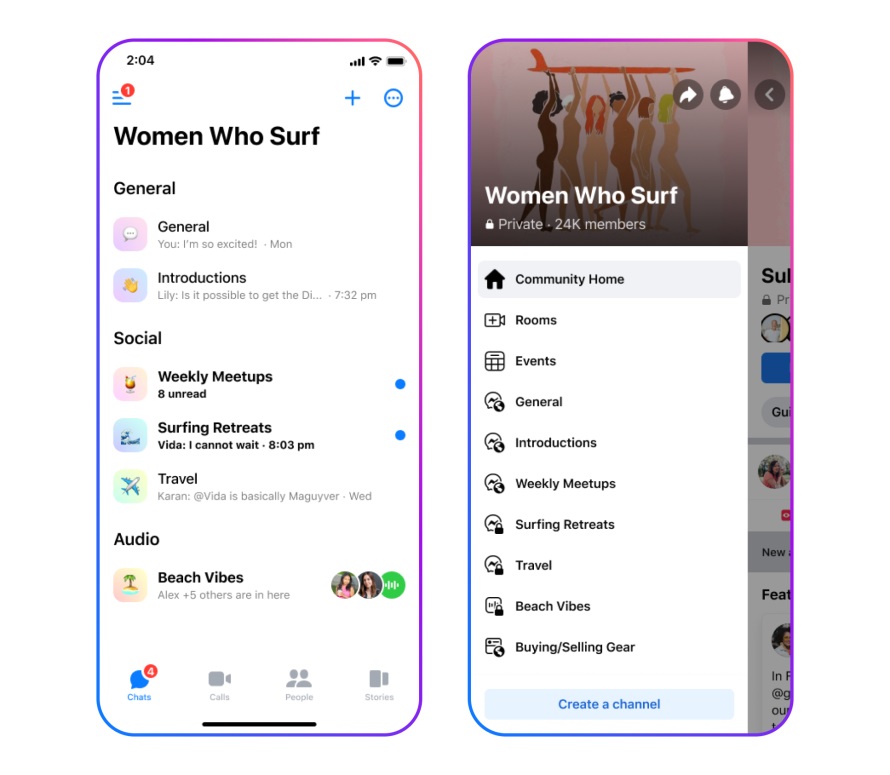
“We will begin testing the ability for people to start Community Chats in Messenger in the coming weeks, allowing people to create a Facebook Group, start chats and audio channels, and invite others to join their new group all within the app.
“We’ll also be expanding Community Chats to even more Facebook Groups,” Mr Zuckerberg announced in the message.
How it works
Admins can choose from several options to help their communities connect. They can start a chat for group members around a specific topic, an event chat for an outing or meetup, a view-only broadcast chat for admins to announce group-wide updates and an admin-only chat to collaborate with admins and moderators.
Admins can also create audio channels so group members can share live commentary or receive real-time support. Participants also have the option to enable video once they’re in the audio channel.
For example, the admin of a Facebook Group for chemistry students could create audio channels for study groups during finals season, and participants can turn on video for live tutoring.
Community Chats are only accessible to members of a group. To learn more about how to use Community Chats, check out the Facebook Community Blog.
Explaining the rationale behind Community Chats, Meta said the feature lets people connect more deeply with communities in real time around the topics they care about in multiple formats, including text, audio and video.
The experience seamlessly blends Messenger and Facebook Groups to allow people to connect when, where and how they want.
Admins can now start a conversation about a topic and get in-the-moment responses instead of waiting for people to comment on a post. And, rather than navigating multiple topics in a single Messenger group chat, the person who creates the Community Chat can organize chats into categories so group members can easily find what’s most interesting to them.
For example, a band’s fan group could have a “Breaking News” category with chats dedicated to new album drops, tour dates and group activities.
“We’re committed to building messaging experiences that help people connect with their communities, friends and families.
“As Community Chats rolls out to more people and groups around the world, we’ll continue exploring new features and capabilities to make it easier to connect with one another,” Mr Zuckerberg stated.
Technology
Airtel Nigeria to Lead Next Phase of Telecoms Growth With Quality of Service Advancements

Airtel Nigeria has unveiled a robust update on a range of network, infrastructure and technology advancements that position the company at the forefront of quality of service leadership in Nigeria’s telecommunications industry. Announced at its first media roundtable of 2026, the updates reflect sustained investments made over the past 12 to 24 months and signal an accelerated push to stay ahead of surging data demand in a rapidly digitising economy.
Speaking to senior editors and industry correspondents, Airtel Nigeria Chief Executive Officer, Dinesh Balsingh, said the company’s strategy is anchored on deliberate scale, depth and resilience.
“Over the last two years, we have invested with discipline and clarity to strengthen our network nationwide. Those investments are now translating into measurable improvements in performance, customer experience and reach, including in underserved and hard to reach communities,” he said. “In 2026, we are accelerating these upgrades because Nigeria’s data appetite is growing, and leadership in this industry will belong to those who plan ahead.”
At the core of Airtel Nigeria’s quality of service drive is the rapid expansion of its network footprint. Since December 2023, the company has increased the number of network sites by 15.5%, adding 2,242 new sites and bringing its total to nearly 16,711 nationwide. Further deployments are planned in 2026 to strengthen coverage, capacity and resilience across urban and rural locations.
Network capacity upgrades have also reached a significant scale. In 2025, Airtel completed capacity enhancements on 30% of its sites, covering over 5032 sites nationwide. Today, 99% of Airtel Nigeria’s sites deliver high-speed 4G mobile broadband, establishing the operator as a full nationwide 4G network. This year, capacity upgrades are being extended to more sites to sustain performance as data usage continues to rise.
According to Chief Technology Officer, Harmanpreet Singh Dhillon, spectrum depth and optimisation remain critical to network quality. “We have increased our 4G spectrum by 10MHz and we are actively optimising our holdings. These actions allow us to support higher data throughput, better speeds and more consistent service, especially in high-traffic areas,” he said.
Airtel Nigeria is also accelerating its 5G rollout. Over the last three months, the company has more than doubled the number of active 5G sites. The accelerated 5G upgrade happening now will connect the top 20 Nigerian cities to high-speed 5G networks, with a significant part of Airtel’s network in these cities becoming 5G-enabled in the coming year.
Beyond terrestrial infrastructure, Airtel is extending connectivity through space-based solutions. The company has established and signed partnerships with satellite providers OneWeb and Starlink, enabling enterprise-grade connectivity for businesses in remote locations, hard-to-reach areas and operational outposts. Recently, Airtel announced Nigeria’s first Direct-to-Cell partnership with Starlink, a breakthrough that will allow customers to remain connected while travelling through deep remote areas and enable small rural communities to access Airtel’s digital and fintech services.
The backbone supporting these services continues to expand. Airtel Nigeria has built an extensive fibre footprint across almost all states, developed through years of sustained deployment. Following the announcement to double capital expenditure last year, the company committed to expanding its fibre network by 25%, and intensive rollout activity is ongoing across cities and states. Airtel has also confirmed plans to extend its fibre footprint even further, both within major cities and between states.
A pivotal national milestone is also on the horizon. Nigeria currently relies on a single internet submarine cable landing and breakout point in Lagos. Airtel Nigeria has announced that it will launch a second internet breakout from the South of Nigeria, leveraging the 2Africa submarine cable. In partnership with 2Africa, Airtel will shortly begin carrying internet breakout traffic from Kwa Ibo in Akwa Ibom State.
“This will create a faster and alternative path for large parts of the North and South, and improve resilience for the entire ecosystem. Airtel is proud to take the lead in making this happen,” Balsingh said.
Underpinning these advances is a robust IT and cloud backbone. Airtel Nigeria operates an enterprise-grade private cloud with thousands of virtual machines, managing massive storage and compute power across locations. The infrastructure includes large GPU clusters, supporting AI-driven applications such as fraud detection, intelligent network self-healing and advanced customer analytics. The company recently announced the upcoming launch of its hyperscaler-ready 38 megawatt data centre in Eko Atlantic. This is designed for Nigeria’s next phase of digital growth, powered by AI.
From a customer access perspective, Airtel Nigeria maintains one of the largest retail footprints in the country. Its products and services are available in over 200,000 outlets nationwide, supported by more than 4,000 exclusive shops across all local government areas and 250 flagship stores.
Balsingh added that, “Quality of service today is about resilience, redundancy and intelligence, and that is what Airtel is delivering. From fibre to cloud to satellite-enabled connectivity, we are building a platform that allows Nigerian businesses to scale with confidence, regardless of location.”
He reaffirmed Airtel Nigeria’s long-term commitment to the country. “Our focus is consistent investment, disciplined execution and deep confidence in Nigeria’s future,” he said.
Aside from Singh Dhillon, other members of the Airtel Nigeria leadership on hand with subject matter expertise at the roundtable included Director, Airtel Business, Ogo Ofomata; Director, Marketing, Ismail Adeshina; Director, Information Technology, Kemi Ariyo; and Director, Corporate Communications and CSR, Femi Adeniran.
Technology
Optasia Commits to Compliance, Ethical Data Use, Respect for Consumer Privacy

By Modupe Gbadeyanka
A global AI-driven fintech platform providing Micro Financing Solutions (MFS) and Airtime Credit Solutions (ACS) to underbanked individuals in 38 countries, Optasia, has reaffirmed its commitment to building long-term confidence across the digital ecosystem through “compliance, ethical data use and respect for consumer privacy.”
At the National Data Privacy Summit to celebrate Nigeria’s National Privacy Week 2026 in Abuja recently, the Chief Commercial Officer of Optasia, Ms Uchenna Agbo, highlighted the heightened responsibility that accompanies rapid digital growth.
“As Nigeria’s digital economy expands, the data that powers innovation and inclusion must be protected with the same seriousness as financial capital,” she said.
Optasia was the official partner of the event themed Privacy in the Era of Emerging Technologies: Trust, Ethics & Innovation.
The seminar brought together regulators, financial institutions and technology leaders. It was convened in line with the Nigeria Data Protection Act (NDPA), which safeguards personal information across the country.
The chief executive of the Nigeria Data Protection Commission (NDPC), Mr Vincent Olatunji, in his speech, underscored the central role of privacy in building trust and unlocking sustainable digital growth.
“Privacy is not an isolated privilege; it is a fundamental right guaranteed by our Constitution. By building trust, we unlock the full potential of our digital economy and protect every Nigerian’s digital identity,” he submitted.
These priorities closely align with Optasia’s approach, as the company focuses on enabling inclusive digital financial services while embedding privacy, accountability and trust into its technology and partnerships.
As a company operating AI-powered financial services within highly regulated environments globally, Optasia brings practical experience in embedding governance, accountability and data protection into large-scale digital systems.
The organisation delivers its services exclusively through licensed financial institutions and regulated distribution partners, supporting the responsible expansion of digital financial services while maintaining robust standards of security and privacy.
Optasia’s SOC 2 Type II certification underscores its commitment to maintaining internationally recognised standards of security, confidentiality, and privacy.
Its Nigeria engagement is anchored in four operating priorities: privacy-by-design, responsible use of AI, innovation without intrusive data practices, and stronger collaboration across the licensed ecosystem.
Technology
The Future of AI Detector Technology in Content Review
AI-written content has already changed how people publish online. Articles, emails, and reports now pass through review systems before going live. Because of this shift, the role of an AI checker free continues to grow. Many users want to know what comes next and how these tools may affect writing in the coming years.
Future detection tools will look different from today’s versions. Current systems rely heavily on surface patterns. That approach is starting to break down as AI writing improves.
Detection Models Will Change Their Focus
Most detectors today analyze predictability and structure. This method worked when AI writing sounded repetitive. Newer AI models now produce varied output. Simple pattern checks will lose value over time.
Future systems will rely more on comparison than pattern spotting. Models may compare writing against known human samples instead of fixed rules. This shift could reduce random false flags.
Context awareness will also improve. Detection tools may evaluate topic flow instead of isolated sentences. That change could help reviewers understand content better.
Training Data Will Update More Frequently
Training data controls detection quality. Older datasets already struggle with newer AI models. Future tools will update training material more often.
More human writing styles will enter training systems. Blogs, emails, and informal writing will receive better representation. This change may reduce bias against simple language.
AI-generated samples will also diversify. Detection systems must understand modern AI behavior. Without frequent updates, reliability will continue to drop.
Scores Will Become Less Central
Percentage scores cause stress for many users. These numbers often create confusion instead of clarity. Future tools may move away from strict scoring.
Visual feedback could replace raw percentages. Highlighted sections may show why something looks artificial. This approach supports editing without panic.
Content reviewers will likely focus on explanation instead of judgment. Guidance helps writers improve clarity rather than chase numbers.
Editing Tools Will Influence Detection Design
Editing tools already affect detection outcomes. A paraphrasing tool can change surface structure without changing meaning. Future detectors may learn to separate helpful edits from mechanical rewriting.
Systems may track rewrite behavior more carefully. Heavy automated paraphrasing may become easier to spot. Manual editing could receive more tolerance.
A summarizer removes depth and context. Detection tools may begin flagging overly compressed structures rather than labeling the entire text. This change would support fairer review.
A grammar checker also affects future detection. Perfect structure often triggers suspicion today. New detectors may learn that clean grammar does not equal automation.
Review Workflows Will Become More Human-Centered
Future content review will likely combine tools and people more closely. Detection systems will guide attention rather than decide outcomes.
Editors may use detection as a starting point. Human review will confirm relevance and intent. This balance protects writing quality.
Writers will also gain clearer feedback. Instead of rewriting blindly, they will understand why something appears artificial.
Regulation and Ethics Will Shape Development
Legal and educational pressure already influences detector design. Schools and publishers demand fairness. Future systems must reduce bias to remain trusted.
Non-native writers face unfair flags today. Improved training may reduce these errors. Ethical design will matter more than raw accuracy.
Transparency will also increase. Users will expect explanations for results. Black-box decisions will lose acceptance.
Limitations Will Still Exist
No detection system will ever confirm authorship with certainty. Human writing varies endlessly. AI writing continues to evolve rapidly.
Future tools may become better guides. They will never replace judgment. Understanding limits will remain essential.
What Writers Should Expect Going Forward
Writers should prepare for guidance-based tools. Detection will assist editing rather than enforce rules. A calm review will replace fear-driven checking.
Natural writing will remain important. Clear ideas still matter more than technical scores. Tools will support this approach rather than punish it.
Final Thoughts
The future of the AI detector points toward smarter review, not stricter judgment. Pattern chasing will fade as context gains importance. Writers and editors will benefit from clearer feedback and fewer false alarms.
Content review will stay human-led. Technology will assist quietly. That balance will define the next phase of writing review.
-

 Feature/OPED6 years ago
Feature/OPED6 years agoDavos was Different this year
-
Travel/Tourism9 years ago
Lagos Seals Western Lodge Hotel In Ikorodu
-

 Showbiz3 years ago
Showbiz3 years agoEstranged Lover Releases Videos of Empress Njamah Bathing
-

 Banking8 years ago
Banking8 years agoSort Codes of GTBank Branches in Nigeria
-

 Economy3 years ago
Economy3 years agoSubsidy Removal: CNG at N130 Per Litre Cheaper Than Petrol—IPMAN
-

 Banking3 years ago
Banking3 years agoSort Codes of UBA Branches in Nigeria
-

 Banking3 years ago
Banking3 years agoFirst Bank Announces Planned Downtime
-

 Sports3 years ago
Sports3 years agoHighest Paid Nigerian Footballer – How Much Do Nigerian Footballers Earn








