Technology
Twitter Thrills Users With Podcasts Feature
By Adedapo Adesanya
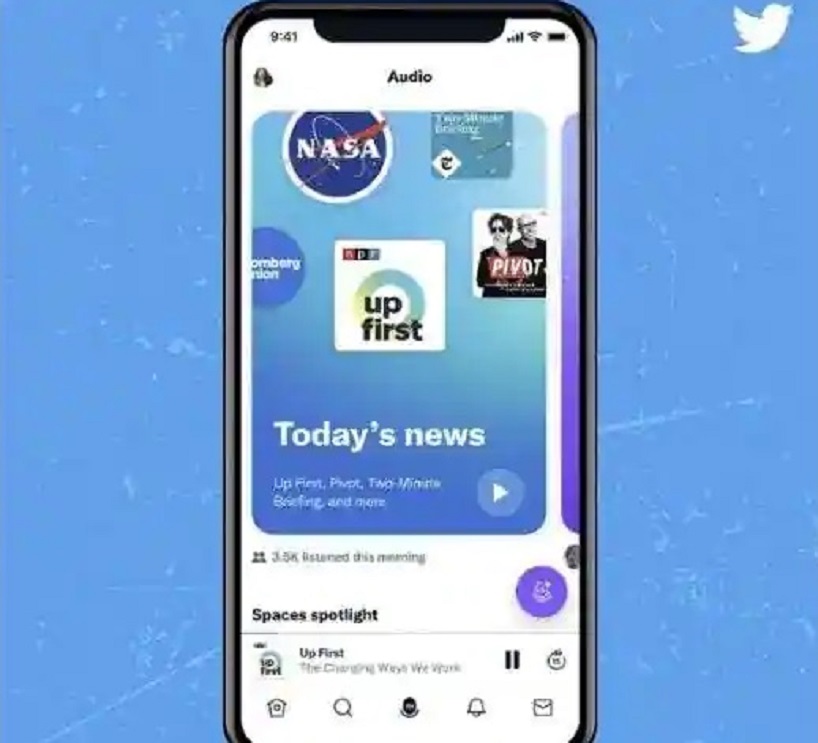
Twitter is officially delving into the world of podcasts as it announced the onboarding of the feature into its platform as part of its newly designed Spaces tab.
Announced in a blog post on Thursday, the social media app is testing a redesigned Spaces tab that groups audio content together by subject, as well as includes podcasts feature for the first time.
The social networking platform explained that, “We know that some discussions need more than 280 characters, and bringing people closer to the ideas, content, and creators they know and love is core to Twitter no matter where the conversations take place.”
It said that integration is another way it is investing in audio creators.
“To do this in a simple and intuitive way that allows listeners to simply hit play and go, we started with a redesigned audio experience in the Spaces Tab.”
This redesign introduces personalized hubs called Stations that group audio content together by specific themes like News, Music, Sports, and more. Now Twitter listeners will be able to easily access a more personalized selection of live and recorded Spaces discussing the topics that are most relevant to them.
Like Twitter’s For You feed, these Stations will be tailored to individual users according to the content and accounts they interact with on Twitter.
Significantly, Stations won’t only include the live and pre-recorded Spaces that Twitter currently hosts, but also suggest pre-recorded podcasts. Users will also be able to help customise the algorithm by giving suggested podcasts a thumbs up or down to indicate their level of interest.
The new Twitter Spaces tab is currently being tested on a select group of English-language accounts.
The revamped Spaces tab and the addition of podcasts are now visible to a group of global English-speaking audiences on iOS and Android.
Twitter says its internal research indicates that 45 per cent of people who use Twitter in the United States also listen to podcasts monthly, so now the company will automatically suggest podcasts to help users discover content based on the topics they’re interested in.
Technology
P2Vest, Others Invest $1.6m in Billboxx for Cash Flow Solutions

By Dipo Olowookere
To tackle the critical cash flow challenges faced by Small and Medium Enterprises (SMEs) across Africa, investors like P2Vest, Norrsken Accelerator, Afrinovation Ventures, Kaleo Ventures, and 54 Collective (formerly known as Founders Factory Africa), have invested about $1.6 million into Billboxx.
The integrated billing-to-payment platform, founded in 2023, successfully closed the pre-seed funding round, which is a mix of debt and equity, due to its innovative approach and commitment to building a more financially secure future for SMEs – the backbone of the African economy.
Manual invoicing and deferred payments often result in delayed payments, stifling many SMEs, but Billboxx’s integrated billing-to-payment platform streamlines billing processes, reduces inefficiencies from manual invoicing and mitigates the impact of deferred payments.
By providing automated billing and invoicing, secure payment facilitation, and tailored cash flow financing, Billboxx empowers businesses to achieve consistent cash flow and focus on growth.
Since its inception, the company has facilitated over $4 million in invoice payments through its MVP launched in May 2023.
The platform boasts strategic integrations with a leading commercial bank in Nigeria, a prominent African payment gateway, and multiple lending partners, enabling seamless payment facilitation via bank transfers, cards, and financing options.
“Cash flow difficulties are the leading cause of business failures in Africa, with delayed invoice payments being a major contributor.
“Billboxx is dedicated to solving these issues with an integrated platform that ensures consistent cash flow and financial resilience for businesses.
“This funding round enables us to expand our impact and empower more SMEs to thrive,” the co-founder and chief executive of BillBoxx, Mr Justus Obaoye, said.
Another co-founder and chief technical officer, Mr Abdulazeez Ogunjobi, noted that, “Delayed invoice payments pose a significant threat to SME growth and survival.
“Our platform not only streamlines the billing-to-payments workflows but also offers strategic embeddings to expedite payments. We aim to alleviate payment concerns and allow SMEs to focus on their core business.”
One of the investors, Bongani Sithole of 54 Collective, said, “We’re enthusiastic about the innovative work the Billboxx team is building. These 3x founders with successful exits under their belts are leveraging their leadership and business experience to tackle a massive pain point for SMEs across Africa.
“We invested in the company due to the large market size of the opportunity, impressive early traction gained from strong early partnerships with notable large corporates and startups, and the solid tech product the team has developed. We’re delighted to back Justus and Abdulazeez as they continue to scale Billboxx.”
Mr Obaoye and Mr Ogunjobi previously co-founded two startups: Charistouch (Carido), successfully acquired by Cars45, and Fixit45, a spin-off from Cars45.
Their leadership experience in large corporations and scaleups such as Schlumberger, Bolt, and OLX add to their strategic insight and entrepreneurial prowess.
Technology
The Rise of Web3 Developers: Why This Career Path is the Future of Tech

As technology advances, the internet is undergoing a revolutionary shift toward decentralization. Known as Web3, this next phase of the internet is redefining how we interact with digital systems by emphasizing transparency, user ownership, and autonomy.
At the heart of this evolution are Web3 developers—professionals whose expertise in blockchain and decentralized systems is driving innovation and creating exciting new opportunities. Pursuing a Web3 career is not just about adapting to industry trends; it’s about shaping the future of technology. In this article, we’ll explore why Web3 developers are in high demand and how you can step into this promising field.
What is Web3?
Web3 represents the decentralized evolution of the internet. Unlike its predecessor, Web2, where centralized platforms dominate, Web3 leverages blockchain technology to create an ecosystem that is transparent, secure, and community-driven.
Some of the defining features of Web3 include:
- Decentralization: Control is distributed among users rather than being concentrated in a single organization.
- Transparency: Blockchain technology ensures that all transactions and operations are open and verifiable.
- Automation: Smart contracts allow for self-executing agreements, reducing the need for intermediaries.
This paradigm shift has unlocked immense opportunities, particularly for developers who can create, manage, and enhance Web3 applications.
Why a Web3 Career is the Future
- Rapid Growth in Blockchain Technology
Blockchain is no longer just about digital currencies; its applications have expanded to include finance, healthcare, logistics, and gaming, among others.
This rapid adoption is driving an unprecedented demand for Web3 developers to build decentralized applications (dApps) and integrate blockchain solutions across various sectors.
- High Demand and Competitive Compensation
The demand for Web3 talent has outpaced supply, making it one of the most lucrative fields in tech. Web3 developers often earn significantly more than traditional developers due to their specialized skills.
Many roles offer remote and flexible working arrangements, enabling global opportunities.
- Opportunities for Innovation
Web3 is still in its infancy, making it a playground for innovators. From creating decentralized finance systems to building virtual economies in the metaverse, developers have the chance to work on groundbreaking projects that redefine industries.
Key Skills for a Successful Web3 Career
To excel as a Web3 developer, mastering certain skills is essential:
- Programming Knowledge: Proficiency in languages like Solidity, Rust, or Go, commonly used in smart contract and blockchain development.
- Blockchain Fundamentals: A deep understanding of how decentralized networks function and their architecture.
- Smart Contracts: The ability to design and implement self-executing contracts.
- Cryptography: Knowledge of encryption techniques to ensure security in applications.
Soft skills such as adaptability and problem-solving are equally important, given the fast-paced nature of the industry.
Benefits of Pursuing a Web3 Career
A career in Web3 comes with a range of unique advantages:
- Global Reach: The decentralized nature of Web3 opens doors to international opportunities without geographical limitations.
- Future-Ready Skills: Web3 expertise is increasingly sought after, offering a secure and sustainable career path.
- Collaborative Ecosystem: Unlike traditional tech environments, Web3 thrives on open collaboration and community-driven development.
- Freedom to Innovate: Developers have the flexibility to experiment and contribute to transformative projects.
Steps to Start Your Web3 Journey
Breaking into a Web3 career may seem challenging, but with a focused approach, it’s entirely achievable. Here’s how to get started:
Understand the Basics
- Learn the core concepts of blockchain technology, decentralized systems, and smart contracts.
- Explore educational resources, tutorials, and online communities for foundational knowledge.
Develop Technical Skills
- Master programming languages and frameworks commonly used in blockchain development.
- Familiarize yourself with Web3-specific tools and libraries to streamline your workflow.
Build Projects
- Start small by creating basic decentralized applications or experimenting with smart contracts.
- Showcase your work in a portfolio to demonstrate your capabilities for a potential employer.
Engage with the Community
- Join forums, developer meetups, and hackathons to network with others in the field.
- Stay updated on industry trends by following Web3-focused discussions and publications.
Continue Learning
- The Web3 space is constantly evolving, so staying up-to-date with advancements is crucial.
- Seek out certifications or courses to deepen your expertise and credibility.
Challenges and Future Outlook
While the opportunities in Web3 are immense, they come with challenges. The fast-evolving technology requires developers to continually upskill. Additionally, the regulatory landscape for blockchain and decentralized systems is still developing, which may introduce uncertainties. A Web3 career offers more than just a job—it provides a chance to shape the next wave of technological innovation. As industries embrace decentralization, the demand for Web3 developers will only grow. Whether you’re a seasoned tech professional or someone looking to enter the field, now is the perfect time to explore this exciting career path. By stepping into the world of Web3, you’re not just advancing your skills—you’re becoming part of a movement that’s redefining how we connect, transact, and collaborate online. The future of technology is here, and it’s decentralized. Will you be part of it?
Technology
HubPharm Wins FCMB HERccelerate Women in Tech Programme

By Adedapo Adesanya
HubPharm has emerged as the winner of First City Monument Bank (FCMB)’s HERccelerate Showcase Day held recently at Hub One, FCMB’s Innovation Hub in Yaba, Lagos.
The tech accelerator, powered by FCMB’s SheVentures and Hub One and delivered by 8thGear Hub & Venture Studios, was designed to empower women-led startups in Nigeria with the skills and resources needed to secure funding and scale.
HubPharm was the best out of 10 finalists with Midddleman, a platform simplifying payments for African e-commerce businesses sourcing from China coming second, while Onit, a productivity tool designed for African SMEs, secured third place.
The Showcase Day brought together the finalists selected from over 1,000 applications who pitched their innovative solutions to a panel of judges.
Ms Tope Kareem, the co-founder of the startup explained that HubPharm is a digital platform with a retail pharmacy chain which has delivered over 100,000 medications across 15 cities, ensuring 98 per cent on-time delivery with AI-driven logistics.
We plan to explore more options and ensure Nigerians, both at home and abroad, know the importance of prioritizing their health. This funding will enable us to keep growing and making an impact,” she noted.
Speaking on the HERccelerate initiative, Mrs Nnenna Jacob-Ogogo, Group Head of SheVentures, described it as “a testament to what we can achieve when we invest in women. While this is the first pilot of its kind, it is clear that women in tech have the talent, resilience, and vision to drive innovation.”
She also highlighted SheVentures’ broader impact, noting that over the past five years, they have “scaled businesses through four key pillars: access to finance, knowledge, markets, and networks. Our Zero Interest Loan program has provided over N800 million in funding to women entrepreneurs so far, an unprecedented achievement in the industry.”
The top 10 finalists will get free access to Hub One’s coworking space for a year, valued at over N5 million and will also be supported to scale their businesses.
FCMB’s HERccelerate programme is setting a new standard for supporting women in tech, with plans to accelerate over 200 startups in the next five years. By fostering innovation and inclusion, FCMB is shaping a brighter future for women entrepreneurs in Nigeria.
-

 Feature/OPED5 years ago
Feature/OPED5 years agoDavos was Different this year
-
Travel/Tourism8 years ago
Lagos Seals Western Lodge Hotel In Ikorodu
-

 Showbiz2 years ago
Showbiz2 years agoEstranged Lover Releases Videos of Empress Njamah Bathing
-

 Banking6 years ago
Banking6 years agoSort Codes of GTBank Branches in Nigeria
-

 Economy2 years ago
Economy2 years agoSubsidy Removal: CNG at N130 Per Litre Cheaper Than Petrol—IPMAN
-

 Banking2 years ago
Banking2 years agoFirst Bank Announces Planned Downtime
-

 Sports2 years ago
Sports2 years agoHighest Paid Nigerian Footballer – How Much Do Nigerian Footballers Earn
-

 Technology4 years ago
Technology4 years agoHow To Link Your MTN, Airtel, Glo, 9mobile Lines to NIN




















