Technology
Umi Blockchain Ecosystem: Instant Transfers, Smart Contracts And Profitable Staking

Thus far, the number of issued cryptocurrencies and digital tokens has exceeded 7,000 and in this ocean of crypto projects, it is difficult for investors to recognize promising services at an early stage of development, however, at the same time, investments at this stage maximize the profits.
UMI is one of the young projects created at the crossroad of DeFi and digital assets trends, which draws attention not only by its unique functionality but also by its future plans.
UMI is a universal monetary instrument that allows users to make instant, secure and free financial transfers, as well as earn crypto through profitable staking.
In addition, UMI is a full-fledged blockchain platform capable of executing smart contracts of any complexity. Let’s take a closer look at UMI capabilities.
Watch a video about UMI below:
Transactions
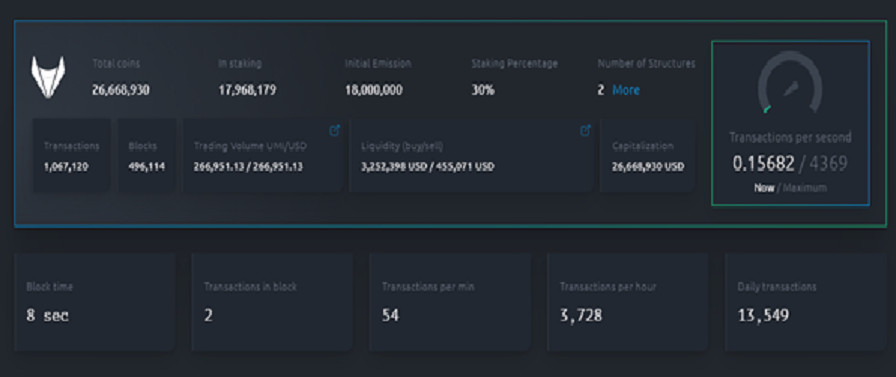
The UMI network can execute approximately 4500 transactions per second. This significantly exceeds the capacity of most other blockchains, including fundamental ones like Bitcoin or Ethereum.
The UMI Mainnet was launched in the summer of 2020 and it’s continuously improving. In the future, the UMI team will roll out an update that will increase enough high capacity to execute 10,000 transactions per second. This brings the UMI platform closer to the transactional conductance of major payment systems such as VISA and MasterCard.
The UMI developers also have a long-term goal – to achieve the capacity of 1 million transactions per second. Although this sounds too ambitious, there is a chance to reach it in the long run, and here is why.
First, the UMI network operates on an improved version of the Proof-of-Authority consensus (PoA consensus characteristics will be discussed in detail later in the article).
Secondly, such scaling can be achieved through the optimization of programming languages and smart contracts, as well as with such tools as Kubernetes.
Finally, upgrades of the UMI network can be carried out faster and with less effort with the planned changes in the internal architecture of the ecosystem.
Another planned function of the UMI ecosystem payment service also appears to be very promising – offline transactions.
Other blockchain systems focus on transactions exclusively via the Internet, while in the UMI ecosystem, the procedure of sending transactions can be carried out without access to the World Wide Web using ordinary SMS or other communication methods.
For example, the length of a UMI transaction is 150 bytes. That’s 1200 bits of information. The standard length of an SMS is 1120 bits (140 bytes), which means that only 2 SMS are required to send a transfer through the UMI blockchain. This is convenient if the transfer needs to be sent urgently, and the Internet is temporarily not accessible.
Technically, the UMI ecosystem is already capable of sending offline transactions without the Internet connection, but the service for initiating transfers has not been launched yet. The UMI team is currently developing it.
Although, the main feature of the UMI blockchain is not the network’s capacity, the absence of any fees. This has been achieved by the unique technology on which the ecosystem is built, as well as a different economic model in comparison to other popular cryptocurrencies.
Technology
The UMI blockchain is based on Proof-of-Authority technology, a concept created by Ethereum co-founder Gavin Wood.
The difference between PoA and the popular Proof-of-Work algorithms (which Bitcoin runs on) or Proof-of-Stake (Ethereum plans to switch to PoS) is that in the PoA network there is no place for the contest between the miners and forgers for the right to generate a block and get a reward.
The generation of blocks, and most importantly, their integration into the blockchain, is handled by trusted nodes – ‘master nodes’. In the UMI network, master nodes are large authorized nodes that meet stringent speed requirements. This feature significantly increases the network’s capacity.
However, the original concept of PoA also has its drawbacks. The original PoA model assumes that ordinary users cannot influence the operating mechanics of the system, and only trusted nodes have the right to confirm transactions and record them in the blockchain, and those usually belong to one organization or affiliated companies. These factors increase the risks of network centralization, which deprives the cryptocurrency of its main value – decentralization – and make it little different from other already existing traditional payment systems.
In order to avoid the risk of network centralization, the nodes in the UMI blockchain are divided into two types – ‘master nodes’, that integrate blocks into the blockchain, and ‘validator nodes’ that validate the blocks. Only certain types of nodes can become master nodes – they include nodes launched both by the UMI team and their numerous partners from different countries, while any user can launch a validator node. Validator nodes monitor the work of the master nodes, and if the suspicious actions are detected, the unscrupulous masters are automatically disconnected from the system.
Along with the distribution of power among master nodes and validator nodes, another mechanism which is designed to prevent centralization is planned to be implemented in the UMI system in the future – integration with Proof-of-Stake consensus.
The UMI blockchain will continue to operate on the PoA algorithm, but if any problems with the master nodes arise, the system will automatically switch to the reserve PoS consensus.
Even if all of the masternodes suddenly stop functioning, the performance of the UMI network and its ability to conduct transactions will not be affected. PoS nodes do not need computing equipment to work, a regular laptop is enough. Any UMI user who has installed a desktop wallet with a validator node will be able to launch a backup PoS node.
Moreover, staking works on a smart contract in the UMI system, which means that the staker does not need to keep the computer on all the time. Thanks to staking on a smart contract, you can generate new UMI coins: up to 40% per month in 24h mode. With such a profitable economic model, UMI encourages users to actively join the system. This model is one of the features that allows UMI to avoid commissions for transfers – staking participants are interested in developing the ecosystem without additional incentives, such as commissions.
Smart contracts
The UMI blockchain allows you to create many specialized multifunctional smart contracts, including those suitable for integration into e-commerce services or for launching decentralized autonomous organizations (DAOs). These include various decentralized finance (DeFi) services.
Areas of application for the UMI blockchain smart contracts:
- Decentralized exchanges and applications;
- DeFi protocols, including Yield Farming and lending;
- Online stores;
- Crowdfunding platforms;
- Gambling sites;
- Gaming platforms;
- Cashback and bonus programs;
- and many other services.
Thanks to its high capacity, the UMI network will ensure the smooth operation of large DeFi projects, decentralized exchanges (DEX) or decentralized applications (DApps), and users will not face unprecedented high transaction fees, as it happened before with the Ethereum network.
Thus, the launch of UMI-based DeFi services will not have a negative impact on those who use the system exclusively for money transfers.
Staking in detail
Currently, UMI coins can be mined in two staking structures (pools) – ROY Club and ISP Club. In order to start mining, you need to create a personal wallet in the UMI blockchain and transfer a certain amount of UMI coins to your address.
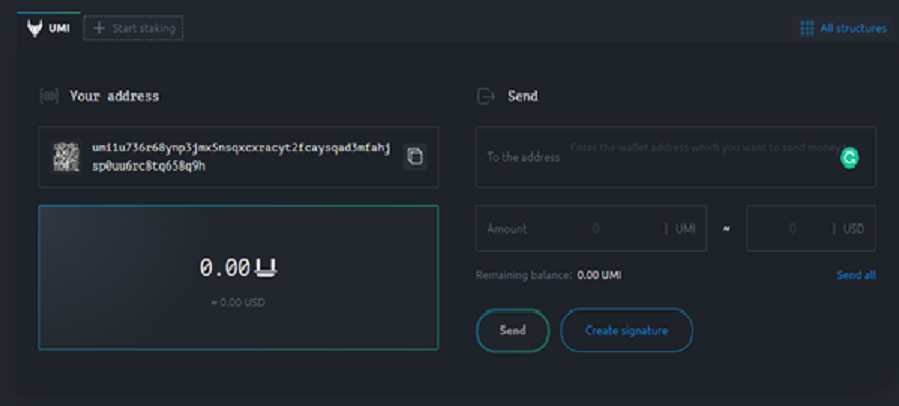
After replenishing the wallet address, you can place your coins for staking in two pools. Unlike other staking systems, coins in the UMI system do not get frozen after joining a pool. They remain in the user’s wallet and no one can access them except the owner. Staking rewards accrue 24/7. The user can withdraw and sell them at any time.
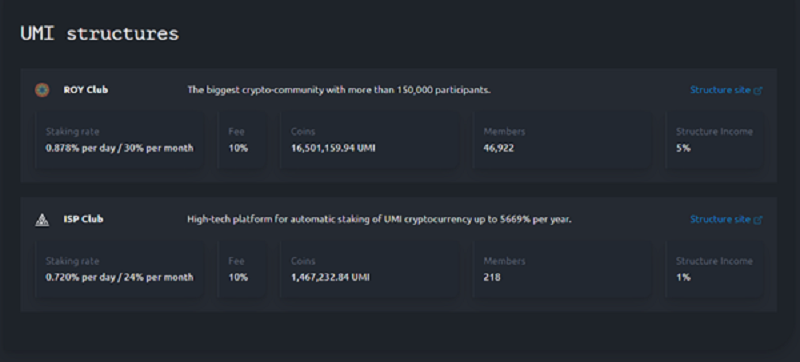
You can buy UMI coins via the SIGEN.pro trading platform, which includes an exchange, an automatic exchanger and a p2p platform. According to the statistics, the daily trading volume of UMI ranges from $ 250,000 to $ 300,000, and the liquidity of the order book for buying coins has already exceeded $ 3.2 million, taking into account the p2p-platform. For the project that was launched only four months ago, the numbers look very promising. The interest in UMI on the market is indirectly evidenced by the rapidly growing number of active users: their number exceeded 47,000.
Mobile apps
Thanks to high-quality and fast mobile apps, users can perform all key operations using a smartphone or tablet. The applications for Android or iOS can be downloaded from Google Play and App Store, respectively.
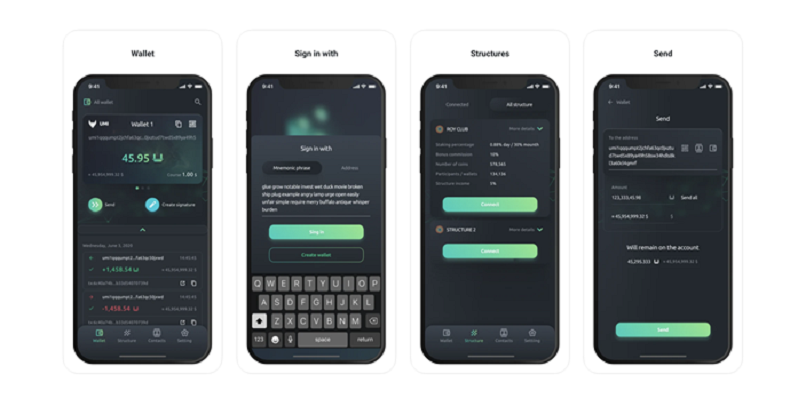
UMI mobile apps offer a wide list of functions. One can create and manage one or several UMI wallets, receive and send coins, connect to staking structures, view the history of transactions and get in touch with technical support.
The applications provide the ability to authorize using Face ID, fingerprint or PIN-code.
You can find all the latest information about the UMI project in the blog.
Technology
Telecom Operators to Issue 14-Day Notice Before SIM Disconnection

By Adedapo Adesanya
Telecommunications operators in Nigeria will now be required to give subscribers a minimum of 14 days’ notice before deactivating their SIM cards over inactivity or post-paid churn, following a fresh proposal by the Nigerian Communications Commission (NCC).
The proposal is contained in a consultation paper, signed by the Executive Vice Chairman and Chief Executive Officer of the NCC, Mr Aminu Maida, and titled Stakeholders Consultation Process for the Telecoms Identity Risks Management Platform, dated February 26, 2026, and published on the Commission’s website.
Under the proposed amendments to the Quality-of-Service (QoS) Business Rules, the Commission said operators must notify affected subscribers ahead of any planned churn.
“Prior to churning of a post-paid line, the Operator shall send a notification to the affected subscriber through an alternative line or an email on the pending churning of his line,” the document stated.
It added that “this notification shall be sent at least 14 days before the final date for the churn of the number.”
A similar provision was proposed for prepaid subscribers. According to the Commission, operators must equally notify prepaid customers via an alternative line or email at least 14 days before the final churn date.
Currently, under Section 2.3.1 of the QoS Business Rules, a subscriber’s line may be deactivated if it has not been used for six months for a revenue-generating event. If the inactivity persists for another six months, the subscriber risks losing the number entirely, except in cases of proven network-related faults.
The new proposal is part of a broader regulatory review tied to the rollout of the Telecoms Identity Risk Management System (TIRMS), a cross-sector platform designed to curb fraud linked to recycled, swapped and barred mobile numbers.
The NCC explained in the background section of the paper that TIRMS is a secure, regulatory-backed platform that helps prevent fraud stemming from churned, swapped, barred Mobile Station International Subscriber Directory Numbers in Nigeria.
It said this platform will provide a uniform approach for all sectors in relation to the integrity and utilisation of registered MSISDNs on the Nigerian Communications network.
In addition to the 14-day notice requirement, the Commission also proposed that operators must submit details of all churned numbers to TIRMS within seven days of completing the churn process, strengthening oversight and accountability in the system.
The consultation process, which the Commission said is in line with Section 58 of the Nigerian Communications Act 2003, will remain open for 21 days from the date of publication. Stakeholders are expected to submit their comments on or before March 20, 2026.
Technology
Silverbird Honours Interswitch’s Elegbe for Nigeria’s Digital Payments Revolution

By Modupe Gbadeyanka
The founder of Interswitch, Mr Mitchell Elegbe, has been honoured for pioneering Nigeria’s digital payments revolution.
At a ceremony in Lagos on Sunday, March 1, 2026, he was bestowed with the 2025 Silverbird Special Achievement Award for shaping Africa’s financial ecosystem.
The Silverbird Special Achievement Award recognises individuals whose innovation, vision, and sustained impact have left an indelible mark on society.
Mr Elegbe described the award as both humbling and symbolic of a broader journey, saying, “This honour represents far more than a personal milestone. It reflects the courage of a team that believed, long before it was fashionable, that Nigeria and Africa could build world-class financial infrastructure.”
“When we started Interswitch, we were driven by a simple but powerful idea that technology could democratise access, unlock opportunity, and enable commerce at scale.
“This recognition by Silverbird strengthens our resolve to continue building systems that empower businesses, support governments, and expand inclusion across the continent,” he said when he received the accolade at the Silverbird Man of the Year Awards ceremony attended by several other dignitaries, whose leadership and contributions continue to shape national development and industry transformation.
In 2002, Mr Elegbe established Interswitch after he was inspired by a bold conviction that technology could fundamentally redefine how value moves within and across economies.
Under his leadership, the company has evolved into one of Africa’s foremost integrated payments and digital commerce companies, powering financial transactions for governments, banks, businesses, and millions of consumers.
Today, much of Nigeria’s electronic payments ecosystem traces its foundational architecture to the systems and rails established under his leadership.
“Mitchell’s journey is inseparable from Nigeria’s digital payments evolution. His foresight and resilience helped establish foundational infrastructure at a time when the ecosystem was still nascent.
“This recognition affirms not only his personal legacy, but the broader impact of Interswitch in enabling commerce and strengthening financial systems across Africa,” the Executive Vice President and Group Marketing and Communications for Interswitch, Ms Cherry Eromosele, commented.
Technology
SERAP Seeks FCCPC Probe into Big Tech’s Impact on Nigeria’s Digital Economy

By Adedapo Adesanya
The Socio-Economic Rights and Accountability Project (SERAP) has called on the Federal Competition and Consumer Protection Commission (FCCPC) to urgently investigate major global technology companies over alleged abuses affecting Nigeria’s digital economy, media freedom, privacy rights and democratic integrity.
In a complaint addressed to the chief executive of FCCPC, Mr Tunji Bello, the group accused Google, Meta (Facebook), Apple, Microsoft (Bing), X, TikTok, Amazon and YouTube of deploying opaque algorithms and leveraging market dominance in ways that allegedly undermine Nigerian media organisations, businesses, and citizens’ rights.
The complaint, signed by SERAP Deputy Director, Mr Kolawole Oluwadare, urged the commission to take measures necessary to urgently prevent further unfair market practices, algorithmic influence, consumer harm and abuses of media freedom, freedom of expression, privacy, and access to information.”
SERAP also asked the FCCPC to convene a public hearing to investigate allegations of algorithmic discrimination, data exploitation, revenue diversion, and anti-competitive conduct involving the tech giants.
According to the organisation, dominant digital platforms now act as private gatekeepers of Nigeria’s information and business ecosystem, wielding enormous influence over public discourse and market competition without sufficient transparency or regulatory oversight.
“Millions of Nigerians rely on these platforms for news, information and business opportunities,” SERAP stated, warning that opaque algorithms and offshore revenue extraction models pose both economic and human rights concerns.
The group argued that the alleged practices threaten media plurality, consumer protection, privacy rights, and the integrity of Nigeria’s forthcoming elections.
SERAP pointed to actions taken by the South African Competition Commission, which investigated Google over alleged bias against local media content, adding that the South African probe reportedly resulted in measures including algorithmic transparency requirements, compliance monitoring and financial remedies.
SERAP urged the FCCPC to take similar steps to safeguard Nigerian media and businesses.
The organisation maintained that if established, the allegations could amount to violations of Sections 17 and 18 of the Federal Competition and Consumer Protection Act (FCCPA), which prohibit abuse of market dominance and anti-competitive conduct.
SERAP stressed that the FCCPC has statutory authority to investigate and sanction conduct that substantially prevents, restricts or distorts competition in Nigeria.
It also warned that failure by the Commission to act promptly could prompt the organisation to pursue legal action to compel regulatory intervention.
Citing concerns reportedly raised by the Nigerian Press Organisation (NPO), SERAP said big tech companies have fundamentally altered Nigeria’s information environment, creating what it described as a structural imbalance of power that threatens the sustainability of professional journalism.
Among the allegations listed are: Algorithms controlled outside Nigeria determining content visibility, monetisation of Nigerian news content without proportionate reinvestment, offshore extraction of advertising revenues, limited discoverability of Nigerian websites and platforms, and lack of transparency in ranking and recommendation systems.
SERAP argued that declining revenues in the Nigerian media industry have led to shrinking newsrooms, closure of bureaus, and the emergence of news deserts, weakening journalism’s constitutional role in democratic accountability.
The organisation further warned that algorithmic opacity and data-driven micro-targeting could influence voter exposure to information ahead of Nigeria’s forthcoming elections, raising concerns about electoral fairness and transparency.
-

 Feature/OPED6 years ago
Feature/OPED6 years agoDavos was Different this year
-
Travel/Tourism10 years ago
Lagos Seals Western Lodge Hotel In Ikorodu
-

 Showbiz3 years ago
Showbiz3 years agoEstranged Lover Releases Videos of Empress Njamah Bathing
-

 Banking8 years ago
Banking8 years agoSort Codes of GTBank Branches in Nigeria
-

 Economy3 years ago
Economy3 years agoSubsidy Removal: CNG at N130 Per Litre Cheaper Than Petrol—IPMAN
-

 Banking3 years ago
Banking3 years agoSort Codes of UBA Branches in Nigeria
-

 Banking3 years ago
Banking3 years agoFirst Bank Announces Planned Downtime
-

 Sports3 years ago
Sports3 years agoHighest Paid Nigerian Footballer – How Much Do Nigerian Footballers Earn













