Technology
The Ultimate Guide to iPhone Hack Texts (2021 Updated)

Texting is more preferred than even calling in recent times. It is becoming an increasingly popular mode and new messaging apps have transformed texts. All the texting apps make it so much entertaining to text.
The year 2020 saw an increase in the usage of texts and messaging. This also brought an increase in search for ‘iPhone hack texts’. With a great demand for iPhone hack apps, there was a lot of competition to cater to it. So, let’s find out which is the best and most reliable way of hacking texts.
Minspy: Best iPhone Hacking App
Minspy is an amazing web-based application. It provides impetus to its users to see the text messages on an iPhone. The highlight of this application is its time efficiency. In just a matter of a few minutes, you can access someone’s iPhone texts remotely.
Minspy also offers a brilliant keylogger feature. This feature allows its users to view all vital keystrokes on the iPhone. You can have a look at the true and holistic picture of the texts. You can see the drafted texts, deleted texts, archived texts and all changes made.
Why Select Minspy?
The competition of spy apps can be bewildering and confusing. As it turns out, there are many players and competitors in the spy industry. Despite the perfect competition, Minspy is class apart. Below are some of the core features that make Minspy stand out:
Stealth Mode
You can spy for as long as you want, you will never be detected with Minspy. The web-based application has been designed in a way that minimizes detection. There will be absolute secrecy of procedures.
The stealth features are nicely embedded into the very functioning. Your spying would be safeguarded. The security is so stern that even Minspy’s own employees would not be able to access any information. This is the kind of security that makes it stand out.
No Jailbreaking and No Rooting
The requirement of jailbreaking or rooting through the iPhone can make one apprehensive. Even if the iPhone users is 1000 miles away from you or even on another continent, you would still be able to hack into their text messages.
Awesome Spying Features
Minspy’s spying features are very simplistic and elite at the same time. Even the premium features of most spy apps do not stand a chance in front of the basic features of Minspy. You can see someone’s messages and you can also see their social media, WhatsApp messages, emails as well.
You can also see someone’s GPS location, notes, calendars, exchange of media and even their browsing history. Anything that is happening on the iPhone, you will be able to see it. Minspy also has abundant features and functions laid out in premium and family plans.

Amazing User Interface
Spy apps can be complicated but Minspy has a great user interface. The user interface is so friendly and convenient to use, you would just know what to do. Even new users at Minspy require any technological prowess to work with the application.
How to Hack Someone’s iPhone Texts
iPhones are expensive because they seem to be very sophisticated. People have a perception that the security of the iPhone is so intact that it cannot be hacked into. Hacking is not only simplified for iPhones but also unbelievably quick. All you need is the right platform.
Minspy is the right platform. It can make one break into an iPhone in under 5 minutes. It is the most coveted, simplified and simplest way to hack into an iPhone. The procedure is just an array of simplistic features that allow hacking into someone’s iPhone texts:
STEP 1: REGISTER WITH MINSPY
As the first and foremost step, you need to log into and sign up for Minspy’s web app. You can sign up through your email ID. This is the only information that will be required from the user’s end to register.
STEP 2: CHOOSE THE DESIRED PLAN
After signing up, you need to select the plan that the user desires. Minspy has a lot of different plans to choose from with distinct features. You can pick the plan that suits you well with respect to the volume and extensity of your hacking.
Minspy has plans like premium and family plans that offer a varied set of features. You can do a quick assessment of your requirement and then pick the perfect plan for yourself.
STEP 3: SETTING UP
After you have selected the plan, you will get an email on your registered email ID. The email will contain the link for setting up the application. The installation would only take a few minutes. Once the setup is complete, you would then need to choose the ‘target platform’.
As the intent is to hack into an iPhone, you need to select ‘iOS’ as the target platform.

STEP 4: iCloud CREDENTIALS
Now, all you need to do is to enter the iCloud credentials of the target iPhone user. That’s the only thing between you and the target iPhone’s messages. As soon as you enter the iCloud credentials, you would be able to link into the target iPhone immediately.
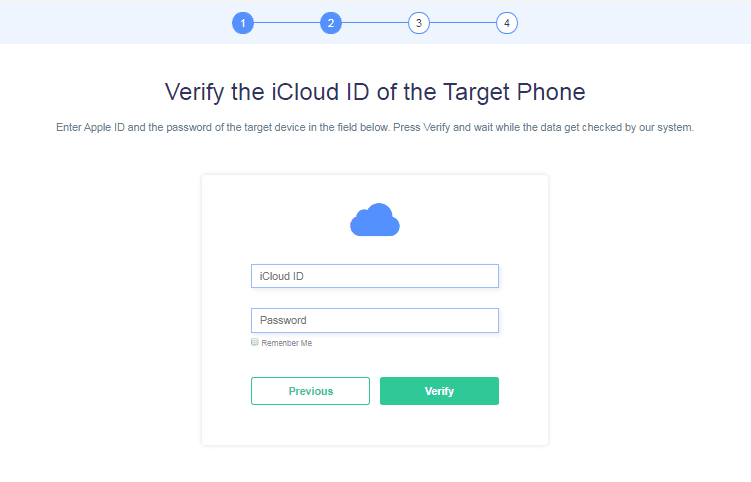 The process will not even take 5 minutes if you have the iCloud credentials in place. It is the most eased out process in place. If you have the required information, it will be easier to spy online than even check the phone for real.
The process will not even take 5 minutes if you have the iCloud credentials in place. It is the most eased out process in place. If you have the required information, it will be easier to spy online than even check the phone for real.
Conclusion
All these functions, features and convenience make Minspy the best-suited alternative for hacking into an iPhone. This platform ensures that iPhone hack texts are done in a much simpler way. It is the most economical hack for reading iPhone texts. So, do not stay in suspense and see for real what is really going on behind the pings.
Technology
Telecom Operators to Issue 14-Day Notice Before SIM Disconnection

By Adedapo Adesanya
Telecommunications operators in Nigeria will now be required to give subscribers a minimum of 14 days’ notice before deactivating their SIM cards over inactivity or post-paid churn, following a fresh proposal by the Nigerian Communications Commission (NCC).
The proposal is contained in a consultation paper, signed by the Executive Vice Chairman and Chief Executive Officer of the NCC, Mr Aminu Maida, and titled Stakeholders Consultation Process for the Telecoms Identity Risks Management Platform, dated February 26, 2026, and published on the Commission’s website.
Under the proposed amendments to the Quality-of-Service (QoS) Business Rules, the Commission said operators must notify affected subscribers ahead of any planned churn.
“Prior to churning of a post-paid line, the Operator shall send a notification to the affected subscriber through an alternative line or an email on the pending churning of his line,” the document stated.
It added that “this notification shall be sent at least 14 days before the final date for the churn of the number.”
A similar provision was proposed for prepaid subscribers. According to the Commission, operators must equally notify prepaid customers via an alternative line or email at least 14 days before the final churn date.
Currently, under Section 2.3.1 of the QoS Business Rules, a subscriber’s line may be deactivated if it has not been used for six months for a revenue-generating event. If the inactivity persists for another six months, the subscriber risks losing the number entirely, except in cases of proven network-related faults.
The new proposal is part of a broader regulatory review tied to the rollout of the Telecoms Identity Risk Management System (TIRMS), a cross-sector platform designed to curb fraud linked to recycled, swapped and barred mobile numbers.
The NCC explained in the background section of the paper that TIRMS is a secure, regulatory-backed platform that helps prevent fraud stemming from churned, swapped, barred Mobile Station International Subscriber Directory Numbers in Nigeria.
It said this platform will provide a uniform approach for all sectors in relation to the integrity and utilisation of registered MSISDNs on the Nigerian Communications network.
In addition to the 14-day notice requirement, the Commission also proposed that operators must submit details of all churned numbers to TIRMS within seven days of completing the churn process, strengthening oversight and accountability in the system.
The consultation process, which the Commission said is in line with Section 58 of the Nigerian Communications Act 2003, will remain open for 21 days from the date of publication. Stakeholders are expected to submit their comments on or before March 20, 2026.
Technology
Silverbird Honours Interswitch’s Elegbe for Nigeria’s Digital Payments Revolution

By Modupe Gbadeyanka
The founder of Interswitch, Mr Mitchell Elegbe, has been honoured for pioneering Nigeria’s digital payments revolution.
At a ceremony in Lagos on Sunday, March 1, 2026, he was bestowed with the 2025 Silverbird Special Achievement Award for shaping Africa’s financial ecosystem.
The Silverbird Special Achievement Award recognises individuals whose innovation, vision, and sustained impact have left an indelible mark on society.
Mr Elegbe described the award as both humbling and symbolic of a broader journey, saying, “This honour represents far more than a personal milestone. It reflects the courage of a team that believed, long before it was fashionable, that Nigeria and Africa could build world-class financial infrastructure.”
“When we started Interswitch, we were driven by a simple but powerful idea that technology could democratise access, unlock opportunity, and enable commerce at scale.
“This recognition by Silverbird strengthens our resolve to continue building systems that empower businesses, support governments, and expand inclusion across the continent,” he said when he received the accolade at the Silverbird Man of the Year Awards ceremony attended by several other dignitaries, whose leadership and contributions continue to shape national development and industry transformation.
In 2002, Mr Elegbe established Interswitch after he was inspired by a bold conviction that technology could fundamentally redefine how value moves within and across economies.
Under his leadership, the company has evolved into one of Africa’s foremost integrated payments and digital commerce companies, powering financial transactions for governments, banks, businesses, and millions of consumers.
Today, much of Nigeria’s electronic payments ecosystem traces its foundational architecture to the systems and rails established under his leadership.
“Mitchell’s journey is inseparable from Nigeria’s digital payments evolution. His foresight and resilience helped establish foundational infrastructure at a time when the ecosystem was still nascent.
“This recognition affirms not only his personal legacy, but the broader impact of Interswitch in enabling commerce and strengthening financial systems across Africa,” the Executive Vice President and Group Marketing and Communications for Interswitch, Ms Cherry Eromosele, commented.
Technology
SERAP Seeks FCCPC Probe into Big Tech’s Impact on Nigeria’s Digital Economy

By Adedapo Adesanya
The Socio-Economic Rights and Accountability Project (SERAP) has called on the Federal Competition and Consumer Protection Commission (FCCPC) to urgently investigate major global technology companies over alleged abuses affecting Nigeria’s digital economy, media freedom, privacy rights and democratic integrity.
In a complaint addressed to the chief executive of FCCPC, Mr Tunji Bello, the group accused Google, Meta (Facebook), Apple, Microsoft (Bing), X, TikTok, Amazon and YouTube of deploying opaque algorithms and leveraging market dominance in ways that allegedly undermine Nigerian media organisations, businesses, and citizens’ rights.
The complaint, signed by SERAP Deputy Director, Mr Kolawole Oluwadare, urged the commission to take measures necessary to urgently prevent further unfair market practices, algorithmic influence, consumer harm and abuses of media freedom, freedom of expression, privacy, and access to information.”
SERAP also asked the FCCPC to convene a public hearing to investigate allegations of algorithmic discrimination, data exploitation, revenue diversion, and anti-competitive conduct involving the tech giants.
According to the organisation, dominant digital platforms now act as private gatekeepers of Nigeria’s information and business ecosystem, wielding enormous influence over public discourse and market competition without sufficient transparency or regulatory oversight.
“Millions of Nigerians rely on these platforms for news, information and business opportunities,” SERAP stated, warning that opaque algorithms and offshore revenue extraction models pose both economic and human rights concerns.
The group argued that the alleged practices threaten media plurality, consumer protection, privacy rights, and the integrity of Nigeria’s forthcoming elections.
SERAP pointed to actions taken by the South African Competition Commission, which investigated Google over alleged bias against local media content, adding that the South African probe reportedly resulted in measures including algorithmic transparency requirements, compliance monitoring and financial remedies.
SERAP urged the FCCPC to take similar steps to safeguard Nigerian media and businesses.
The organisation maintained that if established, the allegations could amount to violations of Sections 17 and 18 of the Federal Competition and Consumer Protection Act (FCCPA), which prohibit abuse of market dominance and anti-competitive conduct.
SERAP stressed that the FCCPC has statutory authority to investigate and sanction conduct that substantially prevents, restricts or distorts competition in Nigeria.
It also warned that failure by the Commission to act promptly could prompt the organisation to pursue legal action to compel regulatory intervention.
Citing concerns reportedly raised by the Nigerian Press Organisation (NPO), SERAP said big tech companies have fundamentally altered Nigeria’s information environment, creating what it described as a structural imbalance of power that threatens the sustainability of professional journalism.
Among the allegations listed are: Algorithms controlled outside Nigeria determining content visibility, monetisation of Nigerian news content without proportionate reinvestment, offshore extraction of advertising revenues, limited discoverability of Nigerian websites and platforms, and lack of transparency in ranking and recommendation systems.
SERAP argued that declining revenues in the Nigerian media industry have led to shrinking newsrooms, closure of bureaus, and the emergence of news deserts, weakening journalism’s constitutional role in democratic accountability.
The organisation further warned that algorithmic opacity and data-driven micro-targeting could influence voter exposure to information ahead of Nigeria’s forthcoming elections, raising concerns about electoral fairness and transparency.
-

 Feature/OPED6 years ago
Feature/OPED6 years agoDavos was Different this year
-
Travel/Tourism10 years ago
Lagos Seals Western Lodge Hotel In Ikorodu
-

 Showbiz3 years ago
Showbiz3 years agoEstranged Lover Releases Videos of Empress Njamah Bathing
-

 Banking8 years ago
Banking8 years agoSort Codes of GTBank Branches in Nigeria
-

 Economy3 years ago
Economy3 years agoSubsidy Removal: CNG at N130 Per Litre Cheaper Than Petrol—IPMAN
-

 Banking3 years ago
Banking3 years agoSort Codes of UBA Branches in Nigeria
-

 Banking3 years ago
Banking3 years agoFirst Bank Announces Planned Downtime
-

 Sports3 years ago
Sports3 years agoHighest Paid Nigerian Footballer – How Much Do Nigerian Footballers Earn












